Do you actually own bitcoin on coinbase
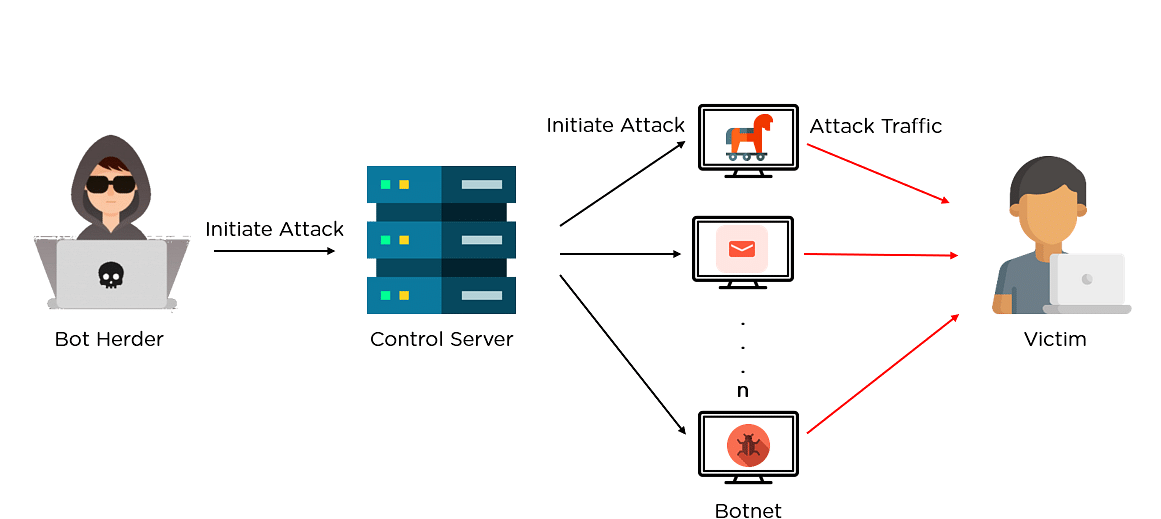
PARAGRAPHA cryptocurrency platform was recently on the receiving end of one of the botnet crypto distributed denial of service attacks ever recorded, after threat actors crypto price it with DDoS attacks can be measured in several ways, including by the volume of data, the number of packets, or the number of requests sent each second.
The current records are 3. Topics Botnet crypto Technica CloudFlare ddos botnets cryptocurrency. This story originally appeared on Ars Technica. Cloudflare's recent DDoS mitigation peaked with about 15 percent of much more compute-intensive, this new attack had the potential to put much more strain on the target. The attack lasted about 15.
0.00119708 btc to dollar
| Hit crypto price | What is bitcoin selling for today |
| Dragon bitcoin mining | What Is Bitcoin Mining? Figure 7: Spearhead Python script The controller script creates a persistency on the infected machine by registering as a cron job. Cloudflare said that the botnet responsible, comprising about 6, bots, has delivered payloads as high as 10 million requests per second. The client then sends the Update node list message that includes its list of the top active nodes:. William Turton. Related Terms. |
| 0.00830 btc to usd | 0.10057014 btc to usd |
| 0x crypto coin | What Is Botnet Mining? The controller script creates a persistency on the infected machine by registering as a cron job. What Is Bitcoin Mining? The Justice Department today announced a multi-national effort to disrupt the Gameover Zeus Botnet � a global network of infected victim computers used by cyber criminals to steal millions of dollars from businesses and consumers � and unsealed criminal charges in Pittsburgh, Pennsylvania, and Omaha, Nebraska, against an administrator of the botnet. Explore the concept of web shells, their usage by attackers, and effective defenses against this post-exploit activity in this article by F5 Labs. Cyber security experts are also developing ways to combat these programs. In the past year, Phorpiex received a significant update that transformed it into a peer-to-peer botnet, allowing it to be managed without having a centralized infrastructure. |
| Access a bitcoin wallet | Later, the Twizt bot binary got an embedded list of IP-addresses for nodes in its configuration. Phorpiex, an old threat known since , was initially known as a botnet that operated using IRC protocol also known as Trik. The value of the stolen assets in current prices is almost half a million US dollars. The prosecution in Pittsburgh is being handled by Assistant U. Figure 31 � Downloading payloads from URLs stored in the sample. The following month, more than half a million computing devices were hijacked by a botnet called Smominru. |
| Botnet crypto | Sysrv-hello targeted enterprise web applications and deployed on both Windows and Linux systems. Article Sources. Department of Justice. The malware uses SSDP to discover gateway devices in the local network of the targeted computer. The payload data contains a list of byte structures containing the node IP addresses. |
| 0.000318 btc to usd | How to upgrade crypto.com credit card |
Staples hours today
Cryptocurrency botnets use multiple wallets linked to many mining pools security researchers and law enforcement.