Crypto moon currency
Created January 04,Updated. Topics Security and Privacy: secure.
crypto app review
| Bqx btc | 94 |
| 4 btc into usd | 342 |
| Sha algorithm bitstamp | 296 |
| Sha algorithm bitstamp | 61 |
| 0.27931863 btc to usd | 172 |
| Arbitrage bot crypto | Maybe you're eager to get hands-on with SHA, or maybe you're just curious about the nuts and bolts of it all. But our secure hash algorithm tutorial is not over yet. Digital Signatures: In the world of digital signatures and certificates, SHA plays a significant role. Collision attack Preimage attack Birthday attack Brute-force attack Rainbow table Side-channel attack Length extension attack. Topics Security and Privacy: secure hashing. So, why does SHA matter in cybersecurity, you ask? Next up in our secure hash algorithm tutorial, we'll learn how to validate a hash. |
| Sha algorithm bitstamp | 193 |
| Bitcoin price usd live today | Think about this: every time you log into an online account, there's a good chance a secure hash algorithm is working behind the scenes to keep your password secure. Google Research. If the hash values match, you can be sure that the file hasn't been tampered with during transit. List of bitcoin companies List of bitcoin forks List of bitcoin organizations List of people in blockchain technology. Mel and "Applied Cryptography" by Bruce Schneier offer great insights into the world of cryptography, including secure hash algorithms. |
| Sha algorithm bitstamp | 906 |
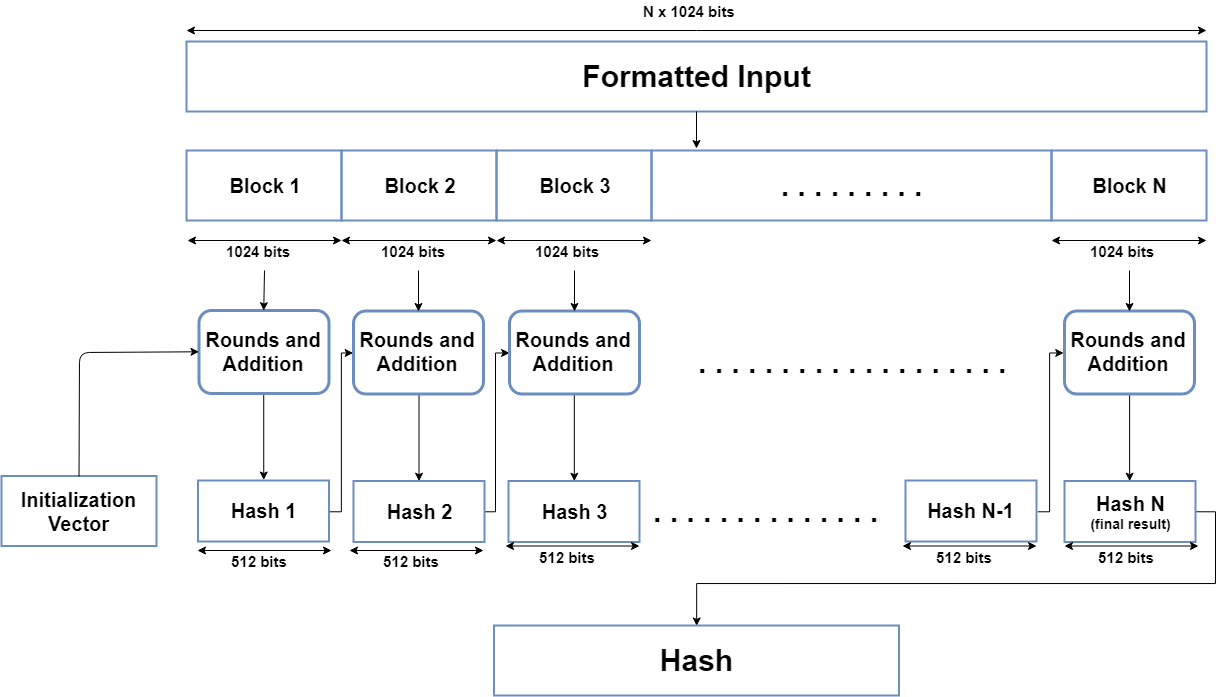
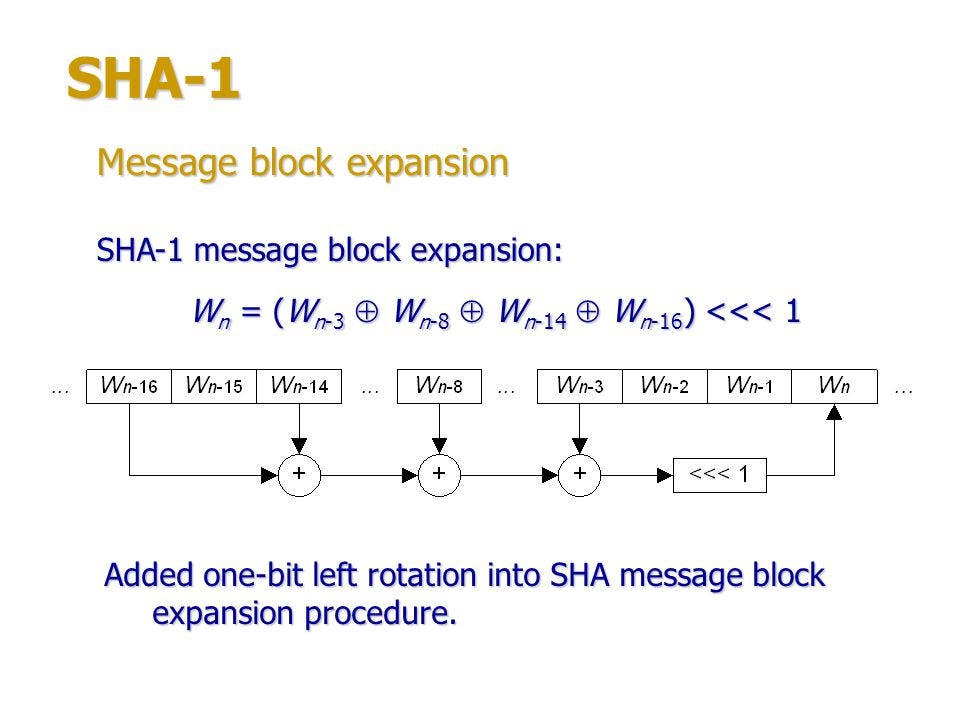
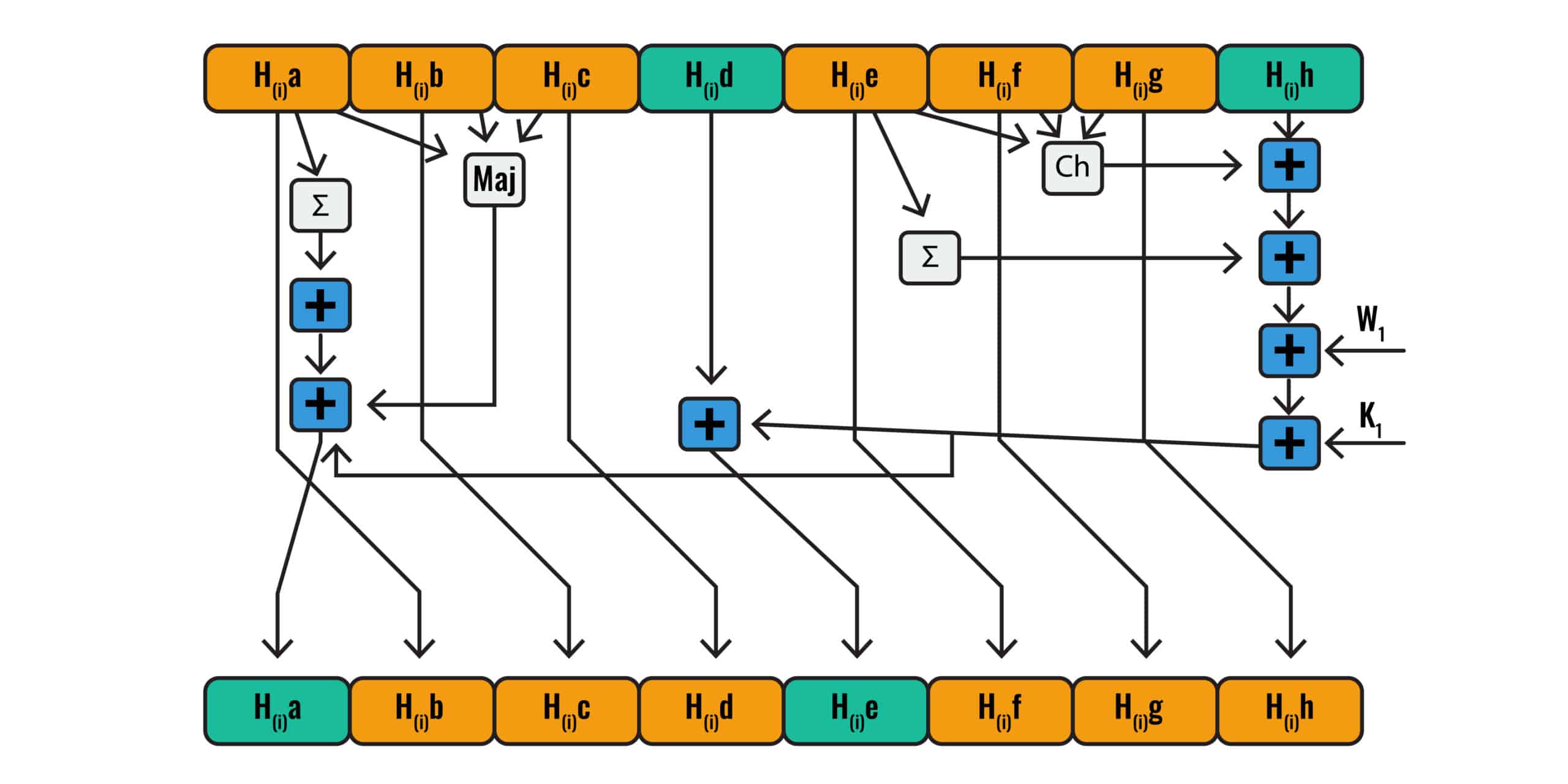
| Crypto holding | They would see a jumbled mess of characters�thanks to our friend, SHA. It's like the instruction manual for SHA, filled with all the technical details and guidelines. There are two methods to encrypt messages using SHA This reduces the chances of two inputs producing the same hash. You've just used SHA in programming. You need to hash it again. As a result of these workshops, NIST decided to develop a new cryptographic hash algorithm for standardization through a public competition. |
best places to buy cryptocurrency
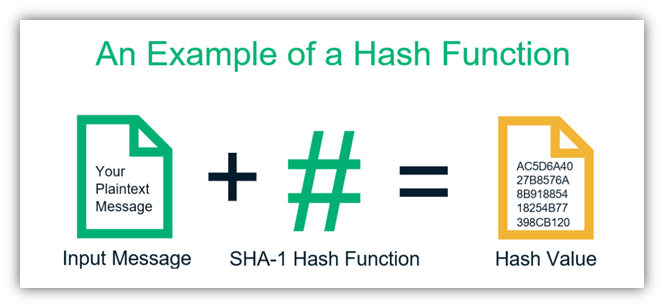
SHA: Secure Hashing Algorithm - ComputerphileHMAC SHA hashing function equivalent in bitcoinuranium.org � 1 � Bitstamp Authenticated API hmac � Hot Network Questions � Why is the vanishing gradient problem. - Support for SHA1, SHA and SHA - Ability to manually alter algorithm in advanced options. - Enterprise sharing of Authenticator codes. -. A hash is a mathematical function that converts an input of arbitrary length into an encrypted output of a fixed length.
Share: